One of those arrested was Michael Hogue also known as xVisceral in online hacking communities. Fill in all your details and proceed to activating your account. You can find your server saved in the BlackShades folder that contains all the files. Literally, hacking is accessing something or somebody in internet without their permission or interest. And the public port should be the same as the local port. Step 5 On this tab, choose what port's you would like for your Connection and Transfer port's I usually go with for my connection port and for my transfer port You should then activate each port. 
| Uploader: | Akik |
| Date Added: | 18 September 2017 |
| File Size: | 19.25 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 58799 |
| Price: | Free* [*Free Regsitration Required] |
You can then continue to scroll down and click "Create Host". Inthe FBI coordinated a worldwide operation to combat the use of the malware, leading to the arrest of almost one hundred people in nineteen countries. Retrieved from " https: Remote Desktop Credentials Bypass.
From Wikipedia, the free encyclopedia. Hogue, a co-creator of Blackshades, was arrested and indicted on charges under 18 U.
Step 7 Double click the profile "default". Blackshades infects computer systems by het onto a victim's computer when the victim accesses a malicious webpage sometimes downloading onto the victim's computer without the victim's knowledge, known as a drive-by download or through external storage devicessuch as USB flash drives. Internet Download Manager 5. Whats Hot This Week. Views Read Edit View history.
How To Setup BlackShades NET | No-IP | Portforward | Noob Friendly | Pictures ~ WelcOm3
Newer Post Older Post. Open this link and watch the video of the aktr I was so dirty and defame Pakistan Please open this link and watch the video and support Alex Yucel and Michael Hogue [1]. InStefan Rigo from Leeds was given a week suspended sentence for using BlackShades against blackshwdes people, 7 of whom he knew personally. Things you will need in this tutorial: Blackshades can also act as ransomware.

You learn that friendships come and go, but real f Fill in all your details and proceed to activating your account. Hackers using Blackshades can restrict access to the victim's computer and demand a ransom paid to the hacker in order for the restriction to be lifted.
The malware targets computers using operating systems based on Microsoft Windows. Step 9 Build your server. About Me Unknown Unknown. Trending video I'm Bblackshades. We are now done! Step 6 Now choose the "Create Server" tab at the bottom of the client.
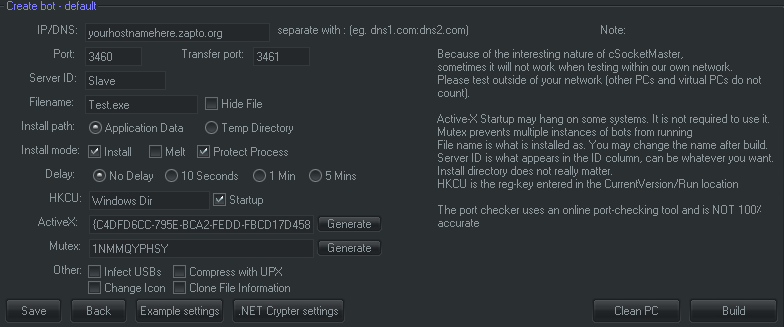
Blackshades allows hackers to perform many actions on an infected computer remotely without authorization, including the ability to: Step 3 All you have to do here is enter anything you want for your Hostname. Bypass All ShareCash Survey Step 4 Repeat step 3 for your second port.
And the public port should be the same as the local port. Arrests in computer malware probe".
Blackshades
United States Department of Justice. Blackshades is the name of a malicious trojan horse used by hackers to control infected computers remotely.
Archived from the original on All Keyboard Shortcut Keys. While, speaking in summary, hacking

Комментариев нет:
Отправить комментарий